Anonymous Email Communication: Tools and Techniques for Privacy
Learn about various methods and tools for maintaining anonymous email communication while protecting your digital privacy.

Anonymous Email Communication: Tools and Techniques for Privacy
People assume email is private. They assume encryption = anonymity. They assume a clever fake address makes them invisible. Those are comforting myths — but comfort is not the same as safety. This guide untangles what anonymous email really means, what’s possible today, and which tools actually move the needle on privacy. I’ll also throw in 10 counterintuitive ideas that should make you rethink your assumptions.
Quick takeaways
- Encryption protects content, not metadata. Even end-to-end encryption (E2EE) can’t hide who sent a message or when, unless you also hide your network identity.
- True anonymity is layered. Use Tor or a VPN + anonymous sign-up + a forwarding/alias service or remailer to reduce traceability.
- No service is magic. Providers may be compelled by law enforcement to hand over logs; design your threat model accordingly.
10 ideas that should challenge your assumptions
-
Encryption ≠ anonymity. E2EE hides message bodies. It does not remove email headers or server logs — the metadata investigators love.
-
A “throwaway” address still leaves breadcrumbs. If you sign up from your home IP or reuse passwords, that alias becomes trivial to link to you.
-
The easiest deanonymization is human error. Attachments, typos, writing style, links to personal sites, or replying from your main inbox are the usual killers — not cryptography failures. (Scholarly Commons)
-
Remailers aren’t dead — they’re niche. The classic Mixmaster/Mixminion remailer tech still works for single-use anonymity, but it’s clumsy for everyday use. (Wikipedia)
-
Alias services (SimpleLogin, AnonAddy) can beat temporary mail for long-term privacy. Temporary inboxes are great for one-time signups; aliases give you control, revocation, and reply capability.
-
Jurisdiction matters — a lot. Two providers using the same crypto can be very different legally. Swiss and German hosts emphasize different protections and legal exposures.
-
You can be anonymous for routine privacy needs — but not for high-risk activism — with the same tools. The difference is operational discipline. Activists need stricter opsec: Tor, air-gapped sign-up, cash payments, and remailer hops. (Whonix)
-
Anonymity is a product of habits, not one tool. A privacy habit stack (separate browser profile, VPN/Tor, aliasing, burner devices) beats any single “private email” provider.
-
Aliases can save you from the “data buffet.” Every site you give your address to is a marketing and breach risk — aliases compartmentalize that risk and make breaches less useful.
-
Expect transparency, not invulnerability. Even privacy champions publish transparency reports and user counts — they want trust, not secrecy. Use that data when picking services.
Related : Check out our guide on when to use temporary emails and sms vs email security
How anonymous email actually works (short primer)
There are three broad strategies people use:
-
Encrypted private providers: Proton Mail, Tutanota, Mailfence, etc. These services provide E2EE or zero-access storage so message content is unreadable to the provider. They ease secure messaging between users but don’t automatically hide network metadata.
-
Alias/forwarding services: SimpleLogin, AnonAddy, addy.io, DuckDuckGo Email Protection. You create per-site addresses that forward to your real inbox; when a site leaks or sells your alias, you can disable it without losing your main address. This is lightweight privacy for daily life.
-
Temporary inboxes & remailers: GuerrillaMail/TempMail do throwaway inboxes; Mixmaster/Mixminion remailers route messages through multiple hops to obfuscate origin. Useful for single interactions or high-anonymity workflows, but limited for long conversations.
LSI keywords to keep in mind while you read on: email privacy, end-to-end encryption, PGP, metadata, VPN, Tor, remailer, email alias, temporary email, header forensics.
Top 10 anonymous email communication providers
- Proton Mail (Proton) — Big, polished E2EE service with Swiss jurisdiction and ecosystem products (VPN, Drive). Notable user base (~100M Proton accounts reported by Proton). (Proton)
- Tutanota — German, open-source, encrypts subject lines and calendars; emphasizes minimal logging and GDPR compliance (celebrated 10M users). (Tuta)
- Mailfence — Belgian service with PGP options and built-in suite (calendar, docs). Good for people wanting compatibility with standard mail protocols. (Mailfence Blog)
- StartMail — Dutch paid provider focused on aliases and privacy (one of the older privacy-first paid options). (HIPAA Compliant Email)
- Mailbox.org / Posteo / Runbox — European, privacy-centric hosts that focus on no-ads and data protection rather than purely on E2EE. (ProPrivacy.com)
- CounterMail / Hushmail — Niche, with specialized features (diskless storage, healthcare compliance). Good for specific workflows. (Lifewire)
- SimpleLogin / AnonAddy / addy.io — Alias and forwarding layers. They’re not full inbox providers but are central to modern privacy stacks. SimpleLogin advertises 1M+ users. (SimpleLogin)
- Guerrilla Mail / TempMail / Mailinator — Disposable inboxes for throwaway signups. Easy but often blocked by sites and unsuitable for sensitive long-term use. (GreyCoder)
- Riseup — Community-run, activist-oriented email with Tor onion services for increased anonymity. Good for tightly scoped use within movements. (riseup.net)
- Remailer networks (Mixmaster, Mixminion) — Not services you sign up for like Proton; they’re protocols and networks used for one-way anonymous messaging. Worth knowing if your threat model demands deep anonymity. (Wikipedia)
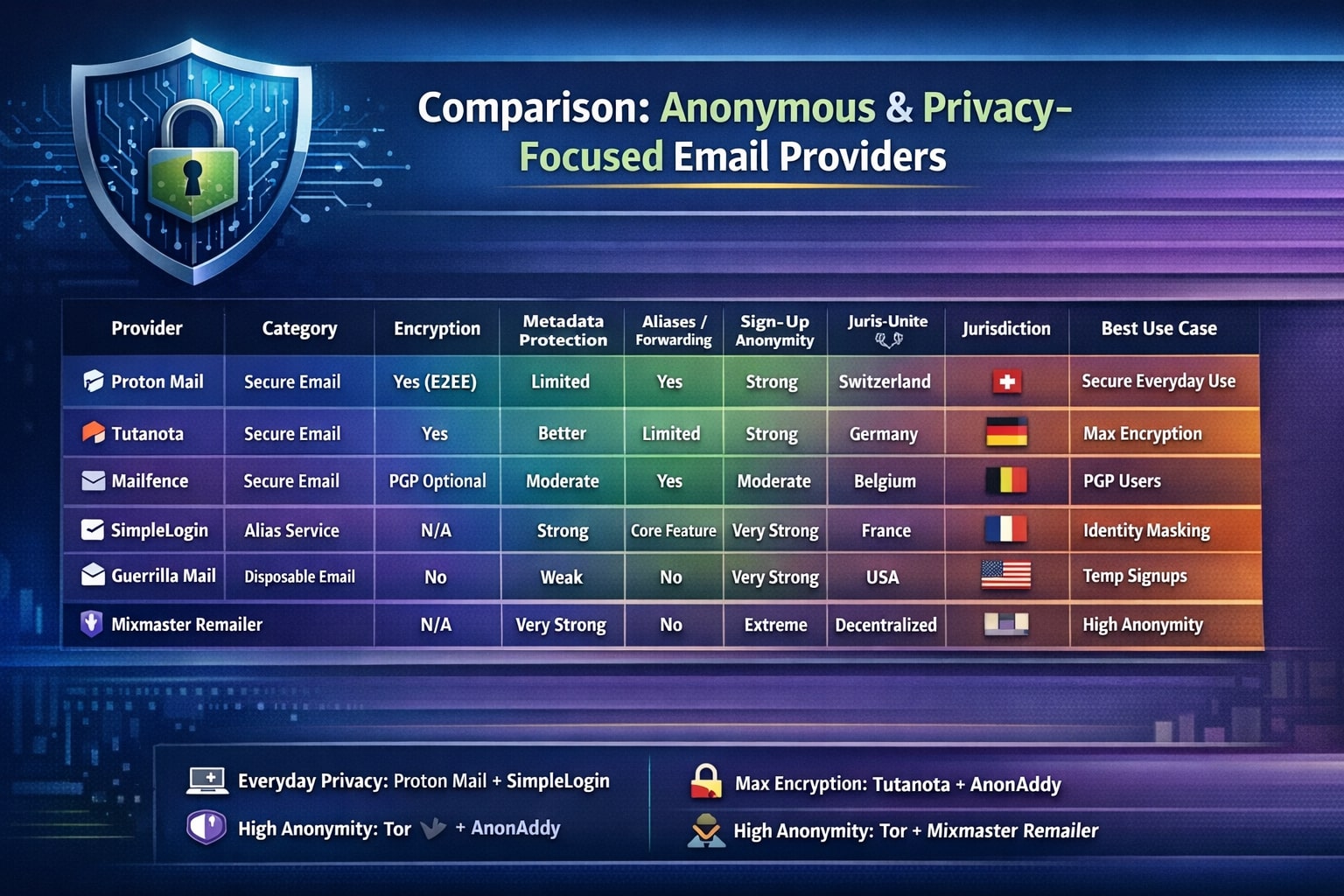
Comparison between Anonymous & Privacy-Focused Email Providers
| Provider | Category | End-to-End Encryption | Metadata Protection | Alias / Forwarding | Sign-up Anonymity | Jurisdiction | Best Use Case |
|---|---|---|---|---|---|---|---|
| Proton Mail | Secure Email Provider | Yes (internal E2EE, PGP support) | Limited (IP logs possible under legal order) | Yes (paid plans) | Strong (no phone required, Tor allowed) | Switzerland | Secure everyday communication with good UX |
| Tutanota | Secure Email Provider | Yes (subjects + body encrypted) | Better than average | Limited (paid) | Strong (anonymous signup possible) | Germany (EU) | Maximum encryption, minimal metadata |
| Mailfence | Secure Email Provider | Optional (PGP) | Moderate | Yes | Moderate | Belgium (EU) | PGP users who want classic email features |
| StartMail | Secure Email Provider | Yes (PGP-based) | Moderate | Strong (unlimited aliases) | Moderate | Netherlands (EU) | Alias-heavy personal or business use |
| Posteo | Privacy Email Host | No default E2EE (PGP optional) | Strong (no IP logging) | No | Very strong (cash payments allowed) | Germany (EU) | Privacy purists, minimalism |
| Mailbox.org | Privacy Email Host | Optional (PGP) | Moderate | Yes | Moderate | Germany (EU) | Business + privacy balance |
| SimpleLogin | Alias / Forwarding | N/A (forwarding only) | Strong (no content storage) | Core feature | Very strong | France (EU) | Identity masking & spam control |
| AnonAddy | Alias / Forwarding | N/A | Strong | Core feature | Very strong | UK | Open-source aliasing |
| Guerrilla Mail | Disposable Email | No | Weak | No | Extremely strong | US | One-time signups |
| Mixmaster Remailer | Remailer Network | N/A (content anonymization) | Very strong | No | Extremely strong | Decentralized | High-risk, one-way anonymous messages |
Practical workflows: low, medium, and high anonymity
Low (everyday privacy): Use an alias (SimpleLogin/AnonAddy) for sign-ups; keep a separate account for newsletters; use a strong password manager and 2FA. This stops tracking and reduces spam quickly.
Medium (sensitive personal matters): Create a Tutanota/Proton account, sign up over Tor or a VPN, pay with privacy-friendly options when possible, use an alias for replies. Avoid attaching identifiable files.
High (activists, whistleblowers): Operate from an air-gapped or separate device, use Tor for everything, sign up to remailer networks or use disposable PGP keys and Mixminion-style remailers, pay in cash or crypto with coin-mixing precautions. This is specialist opsec — mistakes can be catastrophic.
What can go wrong — real examples
Even privacy-first providers have limits. In 2021 French police leveraged Swiss legal channels to obtain IP logs tied to a Proton account; Proton said the content remained encrypted but the IP logs led to an arrest. That episode is a reminder: providers can be compelled to log or hand over metadata under certain legal processes. (TechCrunch)
Forensic investigators routinely use full header analysis, ISP subpoenas, and traffic correlation to deanonymize senders if the adversary has resources. Don’t assume technological wonder will rescue sloppy operational behavior. (Scholarly Commons)

FAQ / People also ask
Is there an untraceable email? Short answer: No single “untraceable” email exists for all threat models. With layered techniques (Tor, remailers, cash payments, air-gapped devices) you can approach practical untraceability for short periods, but powerful adversaries can still correlate traffic and logs.
Is it possible to truly send an email anonymously? Possible, in a narrow sense: one-way messages through remailer chains and Tor can hide the origin for that message. But lasting anonymity over many messages is much harder because of reuse and metadata.
What is a ghost email address? “Ghost email” is colloquial — usually an alias or throwaway address that hides your identity. Think of it as a pseudonymous handle you can disable when it’s been compromised. Aliasing services provide a manageable, revocable way to create ghost addresses.
How safe is anonymous email? It depends on your threat model. For privacy from marketers and data brokers, aliasing + a private provider is very effective. For avoiding nation-state surveillance, you need strict operational security (Tor, remailers, separate devices). No tool is a silver bullet.
Can I hide my email address when sending an email? Yes — by sending through an alias/forwarder or remailer, or by composing through an anonymous provider over Tor. But recipients may still see the forwarding alias or be able to request logs from providers. Again, choose the workflow that fits how strong anonymity must be.
Final notes: pick tools by threat model, not hype
Privacy tech is not a checklist — it’s a stack. Decide what you are defending against (spam, data brokers, employers, or governments), then pick tools that match:
- For spam and tracking: aliases + good password hygiene. (Avoid the Hack (avoidthehack!))
- For confidential conversations: E2EE providers like Proton or Tutanota. (TechRadar)
- For real anonymity against well-resourced adversaries: Tor + remailers + strict opsec (and accept that this is specialist, fragile work). (Whonix)
Which would help you most next?
Explore More Articles
Discover more insights about privacy, security, and digital communication.
View All Articles© 2026 Tempmail.world. All rights reserved.