Email vs SMS Security: Which Communication Channel is Safer?
Email vs SMS security explained: Compare risks, OTP safety, phishing threats, and privacy concerns to learn which communication channel is safer for sensitive information in 2026.

Email vs SMS Security: Which Communication Channel is Safer?
When people ask “is email or SMS safer?” they usually mean one thing: which channel should I trust with my passwords, one-time codes, and private data? The honest answer is: it depends — but not in the way most people think. Security is driven by architecture, threat model, and user behavior, not by whether a message shows up in an inbox or as a green bubble on your phone.
Below I unpack ten counterintuitive ideas that should make you rethink both channels, show the technical and practical reasons behind them, and give clear guidance for everyday protection. This is written for privacy-aware readers and teams that manage authentication, account recovery, or sensitive communications — especially those running disposable/alias email services or advising users to adopt them.
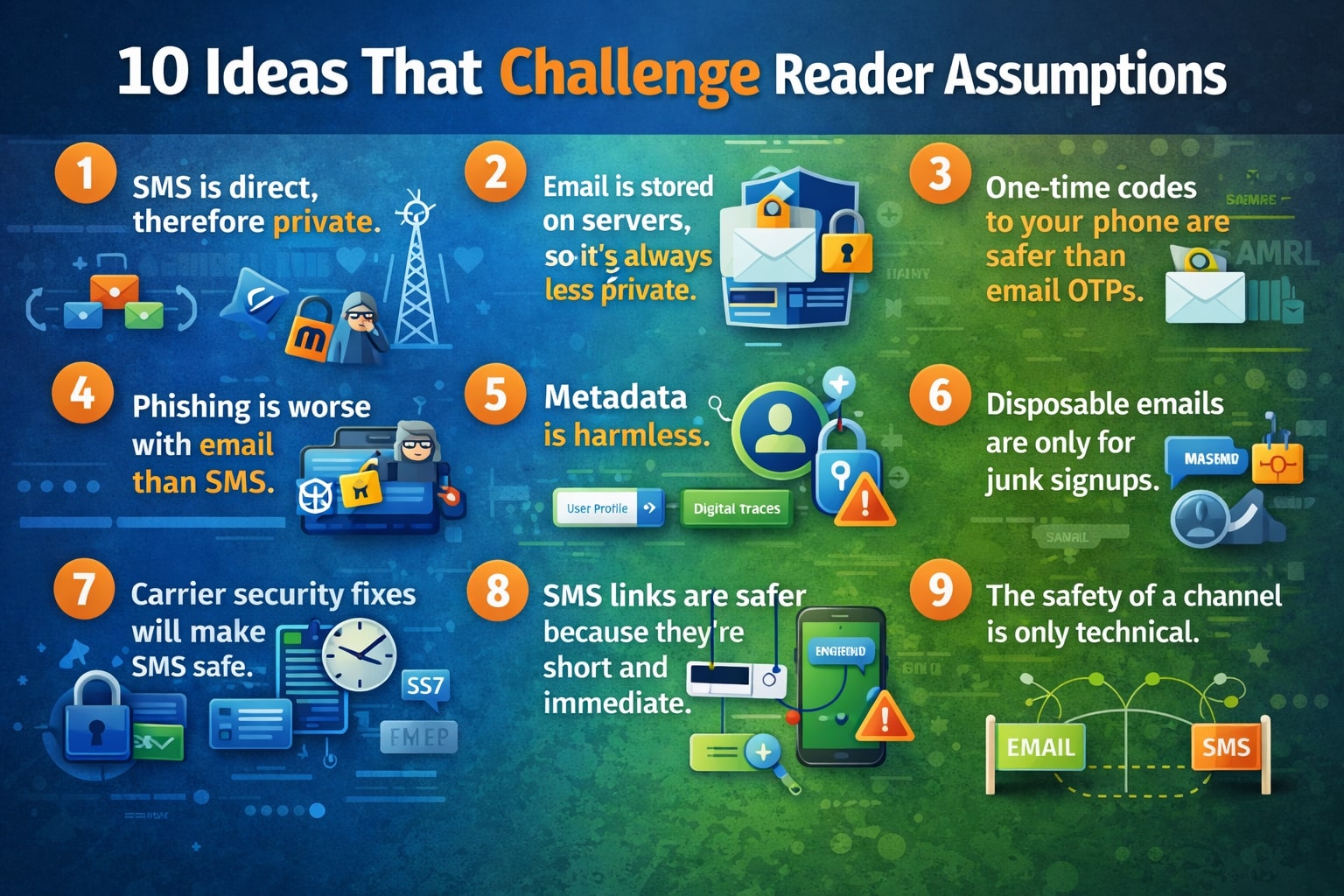
Ten ideas that challenge common assumptions about SMS vs email Security
-
“SMS is direct, therefore private.” — False. SMS travels over carrier networks and telephony signaling systems that were designed for routing and billing, not confidentiality. Modern guidance from U.S. cybersecurity authorities recommends moving away from SMS-based multi-factor authentication because messages are not encrypted end-to-end and can be intercepted via network-level weaknesses. (cisa.gov)
-
“Email is stored on servers, so it’s always less private.” — Not necessarily. While traditional email often transits and rests in servers, email can be end-to-end encrypted with standards like PGP or services that implement zero-access encryption. That option fundamentally changes the security profile in ways SMS cannot match without third-party apps. (Proton)
-
“One-time codes to your phone are safer than email OTPs.” — Outdated. SMS OTPs are convenient but exposed to SIM swap and port-out fraud; attackers can hijack a number and receive codes directly. Regulators and security teams now favour app-based authenticators or hardware tokens over SMS. Large-scale SIM swap incidents have driven this shift. (cifas.org.uk)
-
“Phishing is worse with email than SMS.” — Not always. SMS phishing (“smishing”) has exploded because text messages feel personal and mobile interfaces make it hard to inspect links or sender details. Attackers exploit that trust; a poorly guarded SMS can be far more dangerous than a hashed-out phishing email flagged by a corporate filter.
-
“Metadata is harmless.” — Metadata is a privacy fingerprint. Email metadata can be minimized or pseudonymized (aliases, masked email), but phone numbers are almost always tied to billing identities and location records. That makes SMS far easier to connect back to a real person than many email addresses.
-
“Disposable emails are only for junk signups.” — They’re a broader privacy tool. Alias and disposable email services let you compartmentalize identity across services, limit cross-site tracking, and quarantine breaches — something phone numbers do not do at scale. Masked email and alias forwarding are now mainstream features across privacy-minded providers. (AP News)
-
“Carrier security fixes will make SMS safe.” — Not fast enough. Fixing telephony protocols (SS7, Diameter) and carrier processes is underway, but telecom infrastructure and international interconnects remain a slow-moving, high-friction target for security improvements. Until carrier-side changes are ubiquitous and verifiable, SMS retains structural weaknesses. (cisa.gov)
-
“SMS links are safer because they’re short and immediate.” — Often riskier. Shortened URLs, invisible query strings, and automatic browser opening make mobile links more dangerous. Email clients often add visual clues and spam filtering that help users spot malicious links more readily than native SMS apps.
-
“The safety of a channel is only technical.” — Behavior matters more. A technically secure channel still fails if recoveries and account settings rely on insecure fallbacks (like SMS-based password resets). Strong security is a systems problem: architecture + recovery policy + user practices.
-
“There is a single ‘safer’ choice.” — There isn’t. Context rules. For ephemeral alerts that carry no persistent identity risk, SMS can be acceptable. For account recovery, long-term identity, or transmitting highly sensitive identifiers (SSNs, tax forms), properly encrypted email, aliases, or secure portals are commonly the safer routes.
Practical side-by-side: what the architectures mean
- Encryption: Email can be end-to-end encrypted; SMS cannot. That allows email to protect message contents even if servers or carriers are compromised.
- Identity binding: A phone number is usually directly tied to a legal identity or billing; an email can be pseudonymous or aliased.
- Attack surface: SMS is vulnerable to SIM swap, SS7/Diameter exploits, and carrier-side interception; email is vulnerable to credential theft, phishing, and server breaches — but encryption and aliases reduce impact. (cifas.org.uk)
- Usability: SMS is instantaneous and simple on mobile; secure email (PGP, S/MIME) can be clunky without provider improvements like automatic key lookup or integrated E2EE. That usability gap is closing with privacy-focused vendors.
Latest trends and competitive landscape (top sources considered)
In preparing this analysis I reviewed leading privacy and secure-email providers and public guidance that shape real-world practice: ProtonMail and Fastmail (email encryption and masked email features), Mailfence (enterprise secure email), SimpleLogin and AnonAddy (alias/disposable forwarding), and authoritative guidance from CISA/NIST. The trendlines are clear:
- Enterprise and government guidance is moving away from SMS for MFA and account recovery. Agencies recommend app-based or hardware authenticators and cautious use of SMS. (cisa.gov)
- Secure, privacy-first email providers continue to expand features that make encrypted or alias-based workflows more user-friendly — reducing friction for long-term private messaging. (Proton)
- Masked/alias email use is mainstreaming as a privacy hygiene habit and is now built into major platforms and browsers.
- Check out our guide on temporary email addresses and email security
Short, actionable recommendations
- Don’t send SSNs or similar identifiers over SMS. If you must transmit an SSN, use an encrypted email or a secure portal with zero-access storage.
- Prefer authenticator apps or hardware tokens for MFA. If you must offer OTPs, email is generally preferable to SMS — but authenticator apps are best practice. (pages.nist.gov)
- Adopt email aliases and masked inboxes. Use disposable/alias addresses for signups, marketing, and one-off services to contain exposure.
- Harden recovery paths. Don’t allow SMS-only account recovery. Require additional proof or alternate channels for high-risk account changes. (cisa.gov)
- Educate users on smishing. Teach them to inspect links, verify sender context, and use app-based verification where possible.

FAQ / People also ask
Is it safer to text or email SSN? Neither channel is ideal, but email sent via an encrypted system (or a secure portal) is safer than SMS. SMS lacks end-to-end encryption and is susceptible to carrier-level interception and SIM takeover. Use secure document portals or encrypted email to share SSNs. (cisa.gov)
Is SMS OTP better than email OTP? No — SMS OTP is less secure than app-based authenticators and is often less resilient than email OTPs paired with good email hygiene. Authorities now advise migrating away from SMS for MFA when possible. (cisa.gov)
Are SMS links safer than email links? Generally not. Mobile UIs make it harder to inspect a link’s destination; attackers rely on short URLs and urgency. Email clients provide more clues and spam-filtering, but both channels can carry malicious links — be cautious either way.
Why is SMS not secure? SMS was designed decades ago for simple message delivery, not confidential communication. It lacks built-in encryption, relies on carrier trust, and exposes messages to network-level vulnerabilities (SS7/Diameter) and social-engineering attacks like SIM swapping. (cisa.gov)
What is the safest phone for privacy? Phone model matters less than OS updates, vendor security practices, and the apps you use. Devices that get timely security patches and that you configure conservatively (minimal apps, locked bootloader, strong device passcode, and hardware-backed keys) are the safest. For highly sensitive use, follow guidance to compartmentalize communications (use secure messaging apps like Signal, separate burner devices, and avoid SMS for critical flows). (Help Net Security)
Final word
If your goal is privacy, control, and resilience, treat email and SMS as tools with different trade-offs, not as “good” or “bad” absolutes. SMS is convenient but structurally fragile; email can be much more private when you use encryption and aliases, and it scales better for identity compartmentalization. For authentication and recovery, replace SMS with app-based authenticators and hardware keys wherever possible, and empower users with disposable email and alias options to limit blast radius when breaches happen.
In short: stop asking which channel is “safer” in the abstract. Ask instead: what is the threat, what fallback do we tolerate, and how will we reduce impact when compromise happens? Build communication policies and user workflows around those answers — and you’ll get a lot closer to real safety.
Explore More Articles
Discover more insights about privacy, security, and digital communication.
View All Articles© 2026 Tempmail.world. All rights reserved.